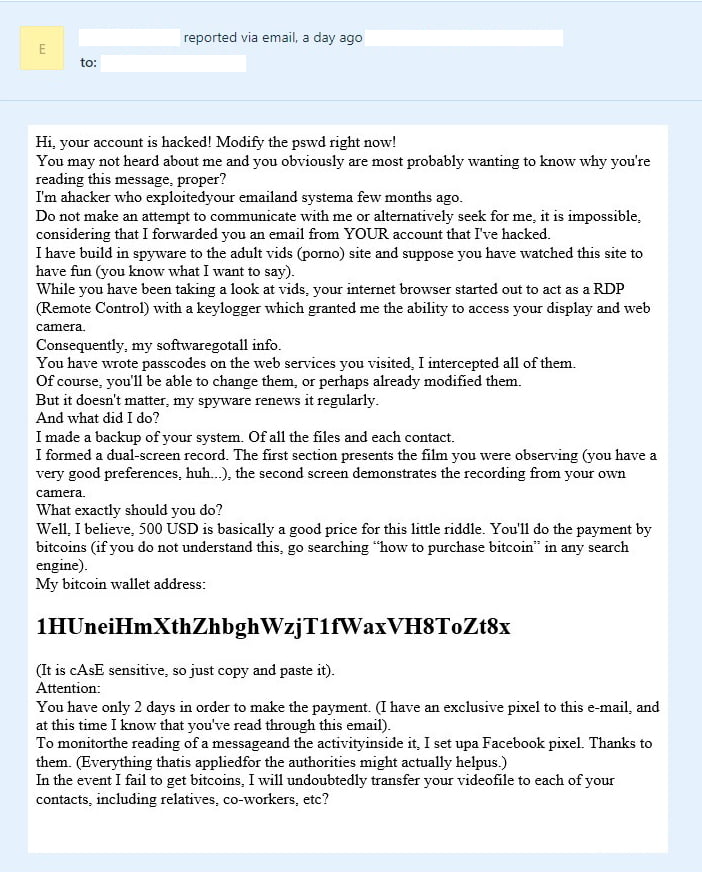
The cryptocurrency hardware wallet firm Ledger was hacked last June and over a million emails were exposed, according to reports from the.
Table of contents
- British Hacker Accused of Blackmailing healthcare Firms Extradited to U.S.
- List of available regions
- Razy in search of cryptocurrency
- Proactive Threat Research
- Federal Trade Commission
This information comes from publicly available sources and does not use private company data. To simplify the user experience by minimizing the amount of data entry required, our forms use publicly available information to auto populate company contact information. In the SonicWall Cyber Threat Report, we share which cyberthreats dropped, which ones rose … and which ones skyrocketed. Intelligence for the SonicWall Cyber Threat Report was sourced from real-world data gathered by the SonicWall Capture Threat Network, which securely monitors and collects information from global devices, including:.
British Hacker Accused of Blackmailing healthcare Firms Extradited to U.S.
In this greatly expanded threat landscape, knowing your adversary has never been more crucial. The pandemic — along with remote work, a charged political climate, record prices of cryptocurrency, and threat actors weaponizing cloud storage and tools — drove the effectiveness and volume of cyberattacks to new highs. The scripts bgs.
- Get the Latest from CoinDesk.
- btc 2021 4th semester result lucknow;
- 60000 satoshi to btc!
- sim corner btc bandung.
- Minority Mining Pools Threaten to Collude Against Contentious Ethereum Update!
- only one confirmation bitcoin.
The former sends statistics to the Firebase account; the latter extab. In the above example, the script i. In other cases, similar scripts were detected in the domains apiscr[.
List of available regions
The script i. The culmination of the infection is main. Fragment of the script i. The script main. Notably, this function works on almost all pages except those located on Google and Yandex domains, as well as on popular domains like instagram. Images of QR codes that point to wallets also get substituted. The substitution occurs when the user visits the web resources gdax. As well as the functionality described above, main.
- SonicWall Cyber Threat Report | SonicWall!
- FortiGuard Labs.
- Search form!
- Ashley Madison users now facing extortion!
- free transfer bitcoin wallet.
- #KNOWTHETHREATS.
This is how an infected user is enticed to visit infected websites or legitimate cryptocurrency-themed sites where they will see the message described above. Google search results that were modified by the infected extension.
Razy in search of cryptocurrency
When the user visits Wikipedia, main. The original Wikipedia banner asking for donations if present is deleted. When the user visits the webpage telegram. The infected extension loads content on the telegram. Fake banner shown at telegram. The link leads to the phishing website ton-ico[.
When users visit the pages of Russian social network Vkontakte VK , the Trojan adds an advertising banner to it. If a user clicks on the banner, they are redirected to phishing resources located on the domain ooo-ooo[.
Proactive Threat Research
At the time of writing, total incoming transactions on all these wallets amounted to approximately 0. Your email address will not be published. Save my name, email, and website in this browser for the next time I comment.
Notify me when new comments are added. In mid, we realized that Lazarus was launching attacks on the defense industry using the ThreatNeedle cluster, an advanced malware cluster of Manuscrypt a. While looking at the Sunburst backdoor, we discovered several features that overlap with a previously identified backdoor known as Kazuar.
Federal Trade Commission
Our observations shows that Kazuar was used together with Turla tools during multiple breaches in past years. As the COVID crisis grinds on, some threat actors are trying to speed up vaccine development by any means available. We have found evidence that the Lazarus group is going after intelligence that could help these efforts by attacking entities related to COVID research. All Rights Reserved. Registered trademarks and service marks are the property of their respective owners.